What is API Security?
Application Programming Interface (API) security is the practice of protecting APIs from attacks. Like databases, servers, and networks, APIs are susceptible to attacks from hackers looking to gain access to sensitive data. Since APIs are more commonly used — to the extent that they’ve become a fundamental part of modern applications — they’ve become a popular target for hackers.
Why is API Security Important?
APIs have found centrality in modern digital architecture because they enable seamless integration of diverse systems, enhancing interoperability and data exchange. This importance means API security shouldn’t be a secondary consideration but a fundamental requirement for data security.
Modern applications rely heavily on APIs to function and communicate with third-party apps and software. APIs allow external clients to request data and services efficiently and seamlessly but carry an inherent security risk. The very capability of APIs that makes them valuable for businesses — seamless data exchange between applications and systems — also makes them an attractive target for hackers, as they introduce more vulnerabilities in the data architecture.
API-related breaches are rising, with 60% of organizations experiencing incidents in the past two years. Of these, 74% faced three or more breaches, and 23% endured over six. These numbers indicate a persistent security gap. The consequences of API data breaches are severe, with affected organizations facing IP theft, financial losses, and brand erosion.
As companies become increasingly dependent on APIs, they are more vulnerable if attacked. A proactive approach to API security is imperative to mitigate the risks and protect crucial and sensitive data transferred between APIs and the systems they interact with.
REST API Security vs. SOAP API Security
REST and SOAP APIs are two popular choices for implementing web services due to their widespread adoption and unique capabilities. REST’s simplicity and flexibility appeal to modern web applications, while SOAP’s robust standards and built-in security cater to enterprise-level systems. Due to their architectural differences, the approach toward their security is also different:
REST API Security
REST (Representational State Transfer) APIs typically use HTTP and rely on mechanisms like HTTPS for encryption, OAuth for authorization, and JWT (JSON Web Tokens) for secure token exchange. Their stateless nature means that applications must authenticate each request individually, enhancing security. REST’s flexibility in choosing security protocols allows for easier implementation but demands careful configuration to prevent vulnerabilities.
SOAP API Security
On the other hand, SOAP (Simple Object Access Protocol) APIs have security built into their protocol with WS-Security. SOAP includes standards for message integrity, confidentiality, and authentication. SOAP can use a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) for encryption. Still, its message-level security ensures the message remains secure even if the transport layer is compromised. SOAP’s strict standards make it inherently more secure but more complex to implement and maintain.
| |
REST API Security |
SOAP API Security |
| Encryption |
Utilizes HTTPS for securing data in transit. |
Uses SSL/TLS for encryption during transport. |
| Authorization and Access Control |
Uses OAuth for handling user authorization, often paired with API keys or Basic Auth for simpler cases. |
Implements WS-Security, which provides a comprehensive framework for message integrity, confidentiality, and authentication. |
| Token-Based Authentication |
Commonly uses JWT (JSON Web Tokens) for secure, stateless token exchanges. |
Typically relies on SAML (Security Assertion Markup Language) tokens or custom XML-based tokens within the WS-Security standard. |
| Security Protocols |
Flexible; can integrate various security protocols and mechanisms as needed. |
Adheres to strict security standards defined by WS-Security. |
READ: SOAP vs. REST: Which API Design is Right for Your Business?
The Role of API Testing in Protecting APIs
API testing allows developers to identify vulnerabilities, ensure reliability, and validate functionality throughout the development lifecycle. Pre-deployment testing, conducted before releasing the API into production, is particularly important as it allows for early detection and resolution of potential issues, reducing the risk of exposing vulnerabilities to users.
Pre-deployment testing helps verify that the API functions as intended, meets the security protocols, and effectively handles various inputs and scenarios.
What are some common API security risks?
Hackers use various tactics to target APIs to exploit weaknesses and access sensitive data. Knowing these methods is crucial for protecting APIs and maintaining system integrity. Some common API security risks include:
- Vulnerability Exploits: Attackers exploit weaknesses in how APIs are built by sending specific data, potentially accessing the API or its application unexpectedly. These vulnerabilities, like SQL injection, can be difficult to address if they’re new and unknown (zero-day threats).
- Authentication-Based Attacks: Methods used to verify client requests can be compromised, allowing attackers to steal credentials or intercept authentication tokens, undermining API security.
- Authorization Errors: Poorly managed access controls may grant unauthorized users access to sensitive data, increasing the risk of breaches. The greater the number of users, the larger the attack surface.
- DoS and DDoS Attacks: Attackers flood APIs with requests, causing service disruptions for legitimate users, a tactic known as denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks.
- Injection Attacks: Injecting malicious code into API requests can manipulate the API’s behavior, potentially exposing sensitive data.
- Weak Authentication: Attackers can exploit vulnerable authentication methods using brute force or session hijacking techniques. Hackers seek broken user authentication to gain access.
- Access Control Issues: Inconsistencies in access control can lead to unauthorized access to resources. Implementing clear access rules is essential to reducing this risk.
Organizations must strengthen authentication and access controls, regularly test for vulnerabilities, and monitor API activity for unusual behavior to mitigate these risks and ensure API security.
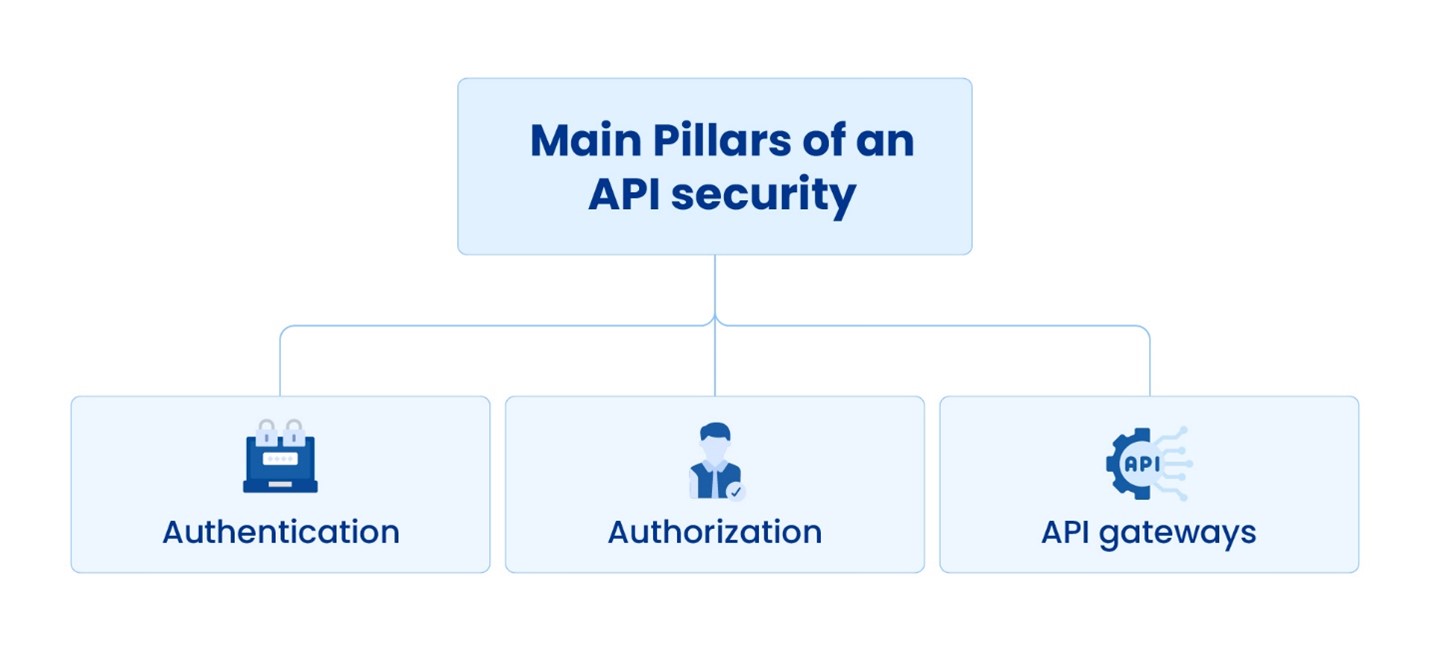
How to Secure APIs and Prevent Vulnerabilities
API gateways, authentication, and authorization are the main pillars of API security, helping to secure APIs and prevent vulnerabilities.
Authentication
Authentication is key to ensuring only legitimate users access APIs. Standard methods include API keys, where each client is given a unique identifier to access the API securely. Another method is OAuth, allowing users to grant specific permissions to applications. Implementing strong authentication measures prevents unauthorized access and protects sensitive data.
Authorization
Once authenticated, APIs must define what actions users can perform. Authorization controls this access, specifying which resources or functionalities each user or client can access. Role-based access control (RBAC) assigns permissions based on user roles, limiting access to only what is necessary. Proper authorization is vital for API security as it protects sensitive data and prevents unauthorized actions.
API Gateways
API gateways act as intermediaries between clients and APIs, providing a centralized entry point for managing requests. They enforce security policies such as authentication, authorization, rate limiting, and encryption. Routing traffic through the gateway allows organizations to monitor and control API access more effectively, reducing the risk of unauthorized access and attacks. Additionally, API gateways offer features like logging and analytics, providing valuable insights into API usage and potential security threats.
What are API Security Tools, and How Do They Protect APIs?
API security tools are designed to protect APIs from threats and vulnerabilities. Top API solutions come with robust security features that primarily focus on authentication, authorization, and documentation to protect sensitive data.
For instance, these tools include API gateways, which serve as a protective barrier between external clients and the API backend, providing security policies such as authentication, authorization, rate limiting, and encryption. Additionally, API firewalls can detect and block malicious requests, preventing common attacks such as SQL injection, cross-site scripting, and API abuse.
API solutions that support pre- and post-deployment testing are invaluable for comprehensive API security. Pre-deployment testing helps identify vulnerabilities and weaknesses in APIs before they go live. Post-deployment testing allows monitoring of the API’s security in the live environment, identifying and addressing any threats or vulnerabilities.
The combination of pre-deployment and post-deployment testing ensures that APIs are thoroughly assessed for security, reliability, and functionality throughout their lifecycle, reducing the chances of breaches and enhancing overall API protection.

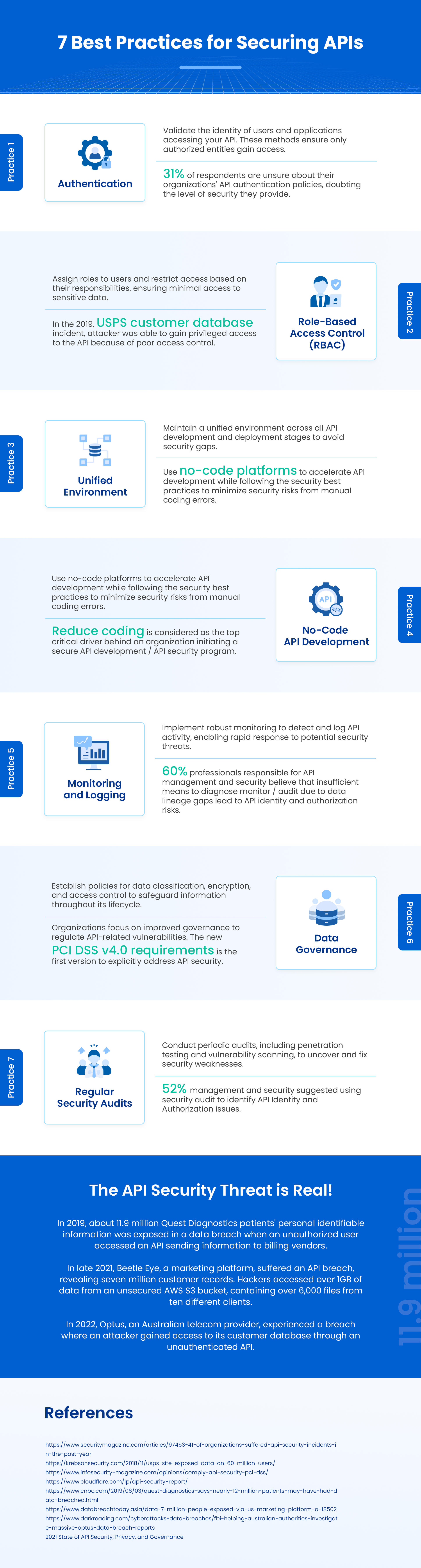
7 API Security Best Practices
It is essential to protect APIs, particularly given the rise of API-dependent applications and systems. The best way to go about it is to follow these API security practices:
- Authentication: Use robust authentication methods like OAuth or API keys to verify the identity of users or applications accessing the API. These methods help organizations ensure that only authorized entities gain access, minimizing the risk of unauthorized access and data breaches.
- Role-Based Access Control: Implement role-based access controls to define and enforce access permissions based on user roles or responsibilities. This approach ensures that users only have access to the resources and functionalities necessary for their roles, reducing the chances of unauthorized access to sensitive data.
- Unified Environment: Maintain a unified environment for API development and deployment to streamline security measures consistently across all stages of the API lifecycle. Standardizing security practices allows organizations to ensure that security considerations are integrated seamlessly into the development process.
- No-Code API Development: Take advantage of no-code API development solutions to simplify and accelerate API development without compromising security. These solutions provide an intuitive interface for creating APIs, reducing the risk of introducing security vulnerabilities through manual coding errors and ensuring that API developers follow security best practices throughout the development process.
- Monitoring and Logging: Ensure robust monitoring and logging to track API activity in near real-time and capture detailed information about requests, responses, and potential security incidents. Monitoring API activity enables organizations to detect and respond to security threats promptly, mitigating the impact of security breaches and ensuring the integrity of API services.
- Data Governance: Establish comprehensive policies and controls to manage and govern API endpoints effectively and protect sensitive information from unauthorized access or misuse. Data governance measures should include data cataloging, classification, encryption, access controls, and regular audits to protect sensitive API endpoints available on the server.
- Regular Security Audits: Conduct regular security audits and assessments to identify and address potential vulnerabilities or weaknesses in the API infrastructure. Security audits should include vulnerability scanning, penetration testing, and reviews to identify security gaps and ensure that security controls are effectively implemented and maintained. API security is a critical data architecture element requiring attention, commitment, and adherence to the best practices. Following the protective measures highlighted above can help safeguard APIs and prevent unwanted access.
As companies continue to depend on APIs to ensure connectivity and data exchange between applications and systems — both internal and outside the organization — investing in a robust API management solution is imperative to ensure protection against threats.
How Astera Ensures API Security
Astera API Management is a no-code, integrated solution that enables you to develop and deploy APIs and integrations. It empowers organizations to do it all: build, manage, test, consume, publish, monitor, and make data more accessible than ever. APIM has a wide range of pre-deployment and post-deployment API testing capabilities to ensure maximum API security.
Pre-deployment testing
Astera’s Instant Data Preview and Preview Raw Request/Response are re-deployment testing and verification of API flows. When designing an API, users can preview and verify the input and output data for each action in the flow. This feature helps identify issues early by testing the API functionality with data during the design phase.
Learn more about this pre-deployment testing feature here.
Post-deployment testing
Astera’s Generate Test Flow option allows users to create post-deployment test flows automatically. These flows use pre-configured API Client and API Connection objects to make live requests to the deployed API endpoints. The API Connection object holds the server’s base URL and an Access Token for authentication. In contrast, the API Client object includes the entire API flow’s logic, from request parameters to response handling.
Learn more about this post-deployment testing feature here.

Astera’s approach to building APIs emphasizes continuous testing and validation. While building an API, users can preview it at every step to ensure it is running correctly. Once the API is fully developed, users can instantly deploy it for testing. APIs can be tested within the Astera platform or via external tools or applications. Users can also leverage Astera’s Automatic documentation to export API collection to outside tools like Postman.
Are you interested in learning more about how Astera supports API testing to ensure maximum application security and exchange data with stakeholders and partners? Schedule a demo to learn more about our code-free API management solution today!
Authors:
 Ammar Ali
Ammar Ali Abeeha Jaffery
Abeeha Jaffery






