
A Complete Guide to Managing Data Access
With organizations prioritizing data-driven decision-making, the amount of collected and stored data is reaching historic highs. Meanwhile, organizations are democratizing access across all functions to convert this data into actionable insights. Since more users will work with sensitive data, ensuring secure access is more important than ever.
Organizations must regulate and maintain the relationship between their data assets and users. Why? First, data integrity is a prerequisite for data to be usable and valuable. Second, organizations need proper data access management and control to protect their data assets from the risk of data breaches and theft.
In fact, according to CrowdStrike, identity-based attack methods are used in 80% of cyberattacks.
So, what exactly is data access management, and why is it important? This blog discusses its types, challenges, and best practices.
What is Data Access?
Data access is the users’ ability to retrieve, modify, move, and share data, typically stored on an offline storage device, a data warehouse, or the cloud.
Data access is all about ensuring that users and organizations can retrieve and utilize the data on demand in an authorized, secure, and convenient manner, whether at rest or in transit.
The modern data stack protects, transforms, analyzes, cleans, and stores data. For modern organizations, data is a commodity almost always in flux, which exposes it to risk-related challenges. This makes proper data access management even more critical.
What Is Data Access Management?
Data access management is crucial to an organization’s overall data management strategy. It involves securing confidential information, defining data ownership, and administering managed access controls.
In other words, data access management involves governing, overseeing, and regulating how data is accessed within an organization. These management protocols also describe the techniques and technologies to access this data.
Data access management is crucial in data governance to ensure safe data retrieval, collaboration, compliance, and ownership.
Importance of Data Access Management
To discuss the importance of data access, let’s return to the modern data stack and its various functions. Data-centric organizations require a host of data management tools functioning in synchronicity. This is integral to creating and sustaining an environment conducive to extracting insights from raw data.
Now, such an array of solutions will facilitate data access, governance, analysis, storage, computing, ETL/ELT, data visualization, and business intelligence (BI).
The organization needs all these functions to work seamlessly for the data to be usable for its users. Proper data access management provides the framework for the data stack to work so organizations can transform data into actionable insights in real-time.
Here are some other benefits highlighting the importance of data access:
Facilitating Information Flow
Data access facilitates smooth information flow, allowing organizations to extract hyper-relevant insights from their data stack. Organizations can have terabytes of data, but to be effective, it should be accessible to the relevant data users. With timely and accurate data access, organizations can improve efficiency, reduce costs, and streamline functions.
Supporting Decision-Making
Similarly, an organization can only make data-driven decisions by providing timely, authorized data access to relevant stakeholders. It’s all about effective data sharing, i.e., putting the right resources in the right hands.
Ensuring Data Security and Compliance
The first aspect of data security and compliance for organizations is active data governance, to meet relevant regulations like GDPR, HIPAA, and CCPA. Organizations should comply with these regulations to uphold data privacy standards and avoid fines and legal consequences.
However, keeping data secure from nefarious elements is also essential. For instance, 2023 saw a 72% increase in data breaches (when compared to the all-time high recorded in 2021). By putting necessary permissions and security levels in place, organizations ensure liberal data access without compromising security.
Democratize Data Access With Astera Data Governance
Astera helps organizations democratize data access while maintaining data security and integrity.
Book a Free Demo to See HowTypes of Data Access
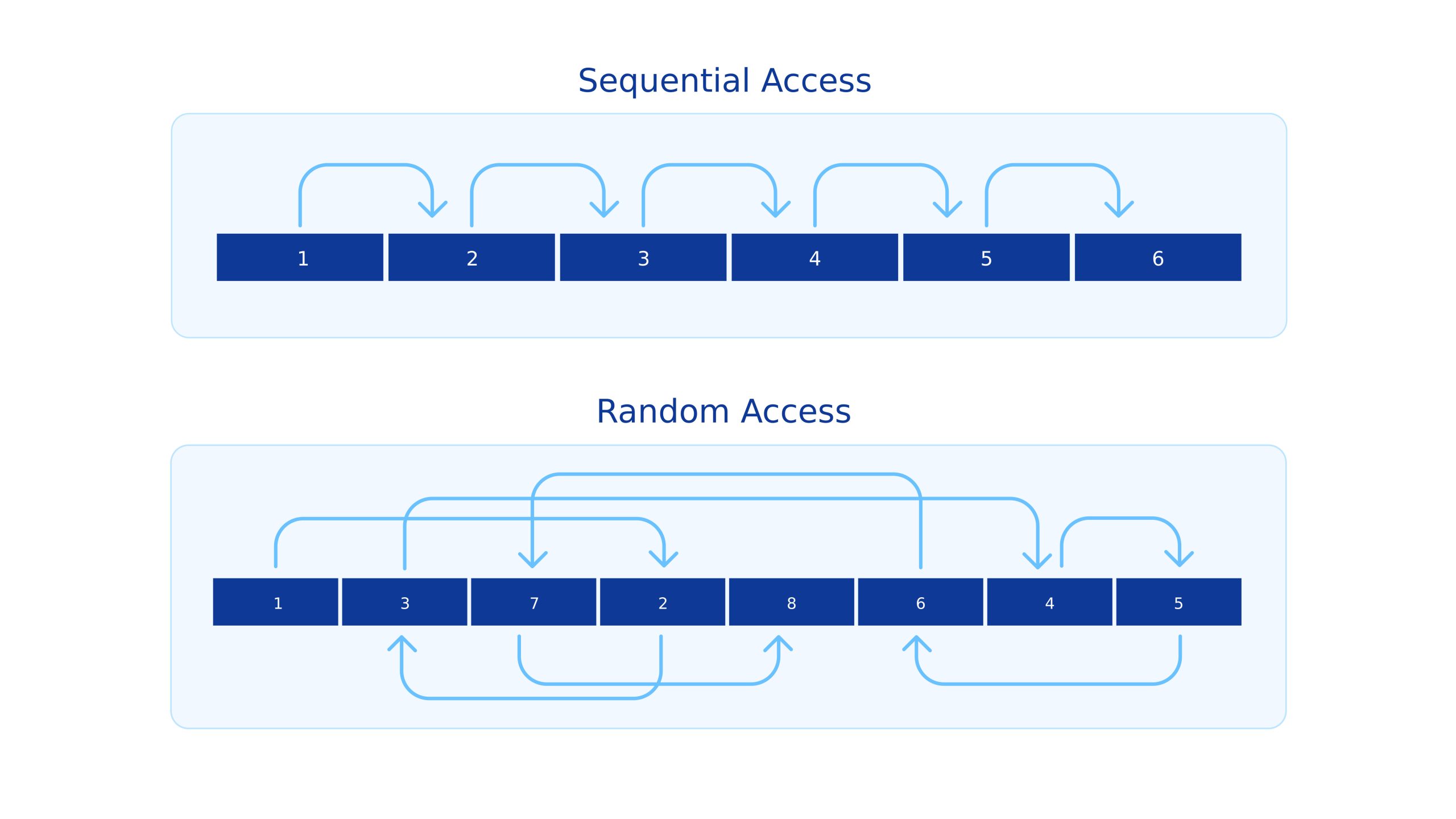
There are two types of data access for data at rest (i.e., stored in a repository or a data warehouse): Sequential Access and Random Access.
1. Sequential Access
Sequential access uses the seek function to move the data on a storage device until it locates the requested data. The defining attribute is that data is read sequentially. This requires higher computational power but is faster than random access as it utilizes fewer seek functions.
2. Random Access
As the name suggests, random access retrieves data from any location on the storage device. This means data doesn’t need to be read sequentially to be retrieved, reducing the computational resource requirement.
Moreover, this method has a fixed upper limit for the retrieval time. Random access becomes the faster option if the fixed time limit is lower than the time required for a sequential read.
Of course, the type of data access will vary depending on the use cases.
Challenges with Data Access Management
Organizations often treat data access management as an afterthought. Even if they prioritize it, they must tackle several data management challenges. Let’s look at some of the biggest challenges in the way of effective data access management:
Managing Access Permissions
Several roadblocks deserve consideration when managing access permissions. For instance, a strict approach can negatively affect data democratization, while a lax approach poses potential security risks.
Moreover, organizations tend to assign access permissions without first classifying their data. Doing so can inadvertently expose sensitive data to unauthorized users or restrict access to useful information, compromising data-driven decision-making.
Furthermore, assigning user-by-user access permissions or allowing users to gain access through data owners can impede access management. This approach is also not scalable, even for smaller organizations.
Managing access permissions is a crucial step in effective data access management. The goal isn’t to lock up data for experts but to make it accessible across the organization to fuel data-led decisions.
Data Privacy and Security Concerns
Data security and privacy typically get overlooked in favor of data integration and democratization in data access management.
However, the writing is on the wall for customer-centric organizations: data security and privacy are non-negotiable. For instance, Cisco reports that 81% of customers believe that how a company handles their data indicates how it views them as customers.
Similarly, a Pew Research study shows that 81% of users believe that companies will use their data in unwelcome ways.
Organizations must prioritize security in all their data activities, the most important of which is data access management.
Handling Data Volume, Source, and Storage Challenges
Approximately 403 million terabytes of data are created every day. The large volume of data from disparate sources is a massive challenge for organizations. Data access management becomes trickier if the data sources aren’t unified.
For example, tracking and controlling access to data becomes progressively difficult when users with access to sensitive data make copies of it and store them in team-specific silos.
Similarly, hybrid data storage solutions mean organizations store data on-premises and in the cloud. Data storage across different locations makes data access even more challenging, as a different set of policies and access permissions may be required for each location.
Best Practices for Data Access Management
Implementing data access is one thing; ensuring frictionless data access is another. Here are some best practices that can help organizations do the latter:
1. Identifying Data Ownership and Location
Identifying where data is stored and who owns the data assets enables organizations to prevent data mistreatment and loss. Organizations can also consider initiating a reward system to incentivize data owners to fulfill their data ownership responsibilities.
2. Implementing Multifactor Authentication
Multifactor authentication lets organizations implement multiple layers of security. Using multiple devices to verify a user’s identity ensures anyone hoping to breach cannot bypass all the security levels.
Organizations can also consider varying the authentication methods depending on the sensitivity of the data assets. For instance, OTPs and authenticator apps can be used for business-sensitive data. In contrast, biometric controls are good options for PII.
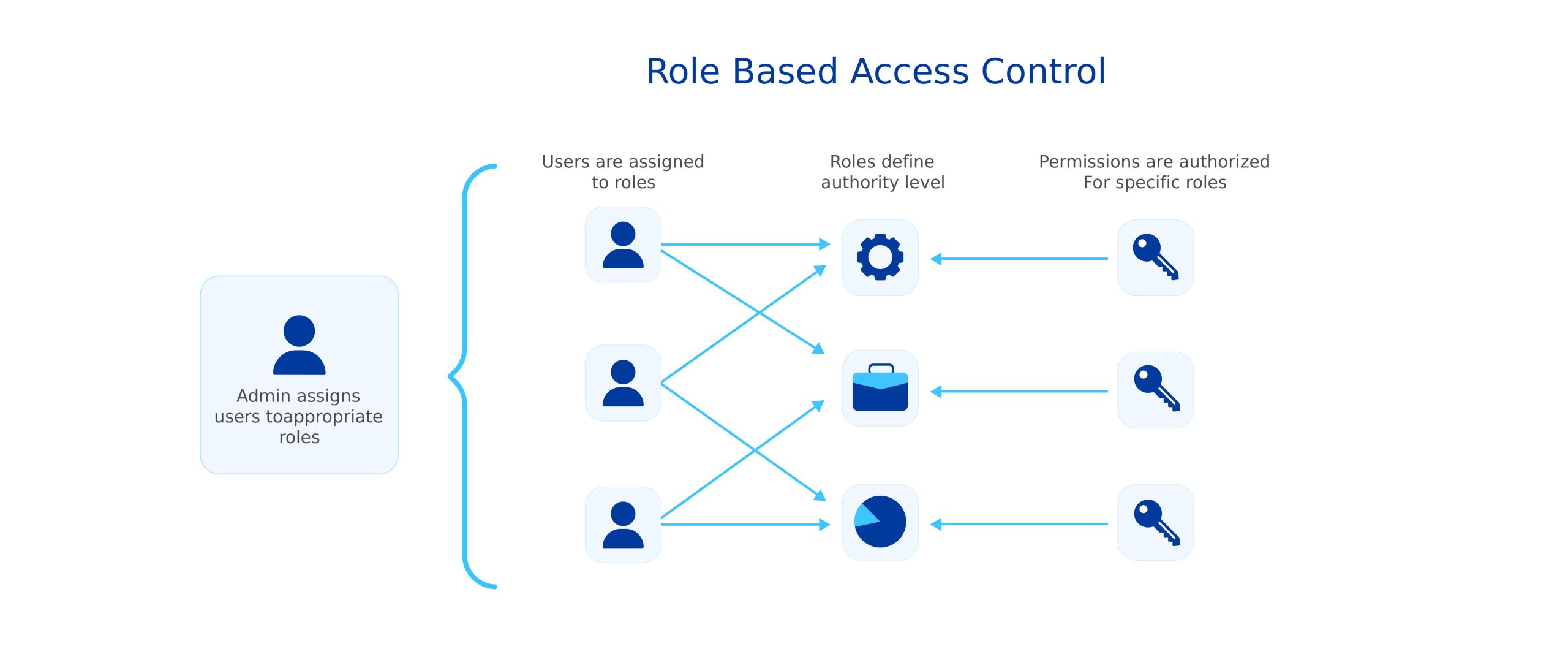
3. Using Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) involves assigning access to sensitive data based on the user’s role in the organization.
For instance, administrators can restrict or grant access to users by assigning them relevant roles based on their titles and departments. These roles define authority levels, restricting and granting access to data assets accordingly.
4. Creating Security Groups
Creating a series of security groups can help organizations oversee and implement their data access measures. These groups should include representatives from domains that typically work with data assets.
Security groups assess an organization’s data access needs and grant access to sensitive data on a case-by-case basis. They decide the level of access to be granted to different users while assessing and implementing data access policies within the organization.
5. Regularly Auditing Data Access
Putting proper data access protocols in place is only half the battle. Audits of the activities of data owners and users offer insights into the strategy’s success and areas for improvement. Organizations can make changes on the go and calibrate their access management strategy by conducting regular audits.
Concluding Thoughts
Organizations looking to democratize data sharing across their business functions cannot do so without proper data access management. By prioritizing data access management, organizations improve data privacy, security, integrity, and compliance in their data management.
As a data management solution, Astera simplifies access to data scattered across disparate sources by providing a unified, user-friendly platform. With Astera, organizations combine their data easily and make it accessible to their data users for:
- Data consolidation from disparate sources into a single repository.
- Efficient extraction, cleansing, transformation, and validation of large volumes of data.
- Building a single source of truth for BI reporting and analytics.
Astera’s data governance capabilities make access management easy by centralizing access to data assets while specifying their type, ownership, and creation details. The granular access management lets organizations protect their sensitive information by streamlining permissions for relevant users.
Modernize your data access management with Astera’s AI-powered data platform. Get your personalized demo today.
 Astera AI Agent Builder - First Look Coming Soon!
Astera AI Agent Builder - First Look Coming Soon!


