
Exploring Data Provenance: Ensuring Data Integrity and Authenticity
What is Data Provenance?
Data provenance is a method of creating a documented trail that accounts for data’s origin, creation, movement, and dissemination. It involves storing the ownership and process history of data objects to answer questions like, “When was data created?”, “Who created the data?” and “Why was it created?
Data provenance is vital in establishing data lineage, which is essential for validating, debugging, auditing, and evaluating data quality and determining data reliability.
Data Lineage vs. Data Provenance
Data provenance and data lineage are the distinct and complementary perspectives of data management. Data lineage mainly provides a high-level trail of data’s journey (from origin to consumption), including any changes made.
Data provenance is what adds depth to this trail. It tells us about data’s origins and the changes made to it and provides insights into who created the data, made those changes, data quality, etc.
Learn more about the differences between data provenance vs. data lineage.
The Importance of Data Provenance
Data provenance is a fundamental requirement for ensuring trust, reliability, and efficacy of data-based decision making.
Opaque Data Pipelines
The growing complexity of modern data systems and pipelines makes it difficult to track data lineage. Businesses lack complete visibility into how data is transformed and moved across various systems, creating a blind spot for potential issues.
Data provenance empowers businesses to understand how data flows through their systems by revealing data’s origin, transformations, and movements. This transparency allows for proactive identification of potential issues before they escalate.
Data Quality Concerns
Without clear data lineage, identifying inconsistencies and anomalies becomes a time-consuming task. Errors or biases can go undetected, potentially leading to flawed decisions with significant consequences.
Data provenance facilitates the detection of anomalies and inconsistencies within data. By tracing the lineage, businesses can pinpoint the source of errors and correct them proactively to ensure data integrity.
For instance, when a sales dashboard shows a sudden revenue spike, data provenance identifies where the anomaly started, facilitating quick resolution and preventing faulty data from affecting decisions.
Navigating Regulations
The rapid increase of data privacy regulations like GDPR and HIPAA mandates that organizations demonstrate responsible data governance. Data provenance enables organizations to prove their compliance with these regulations.
In an audit, data provenance offers a clear trail that details the origin and handling of sensitive data, reducing potential legal issues and building trust with stakeholders.
Empowers AI and Analytics
The effectiveness of artificial intelligence (AI) and data analytics relies on the quality and trustworthiness of data. Data provenance enables scientists to identify biases or inconsistencies that could distort model outputs by tracing data lineage.
Also, it supports explainability in AI decision-making, tracing back to how the AI reached its conclusions.
The Role of Data Provenance in Ensuring Data Integrity and Authenticity
Verifying the Origin and Lineage
Data provenance creates a verifiable data custody chain. It records data sources and all transformations, helping organizations spot and address potential impurities in data.
For instance, an organization collects customer data from various sources and merges it into a single database. Data provenance verifies the origin of each data stream, ensuring the data remains untampered and free from inaccurate information during collection. This careful tracking builds trust in the data’s authenticity by allowing easy source verification.
Detecting Unauthorized Modification
It also helps organizations detect and prevent unauthorized changes by tracking changes to data points, making anomalies and inconsistencies visible.
For instance, if a financial record changes unexpectedly, data provenance flags it for investigation. This process helps catch and fix unauthorized access or manipulations early, protecting data integrity. It also supports access control by tracking who interacts with data and pinpointing those responsible for changes.
Facilitating Reproducibility and Auditability
Reproducibility is the ability to replicate research and analytical results. Data provenance records the data used, its changes, and the analysis processes, allowing researchers to recreate a study’s original conditions accurately. The accurate replication prevents the spread of incorrect or misleading findings by allowing the independent verification of results.
Data provenance also supports auditability by providing a clear audit trail for regulatory reviews or compliance audits.
Identifying Errors in Data Pipelines
Data lineage tracking enables organizations to spot and fix errors and biases in data pipelines. For example, if a loan approval algorithm shows bias against certain demographics, data provenance lets data scientists examine the training data.
They can find and correct biases introduced during data collection or transformation. This process improves data pipelines, making them more accurate and fairer.
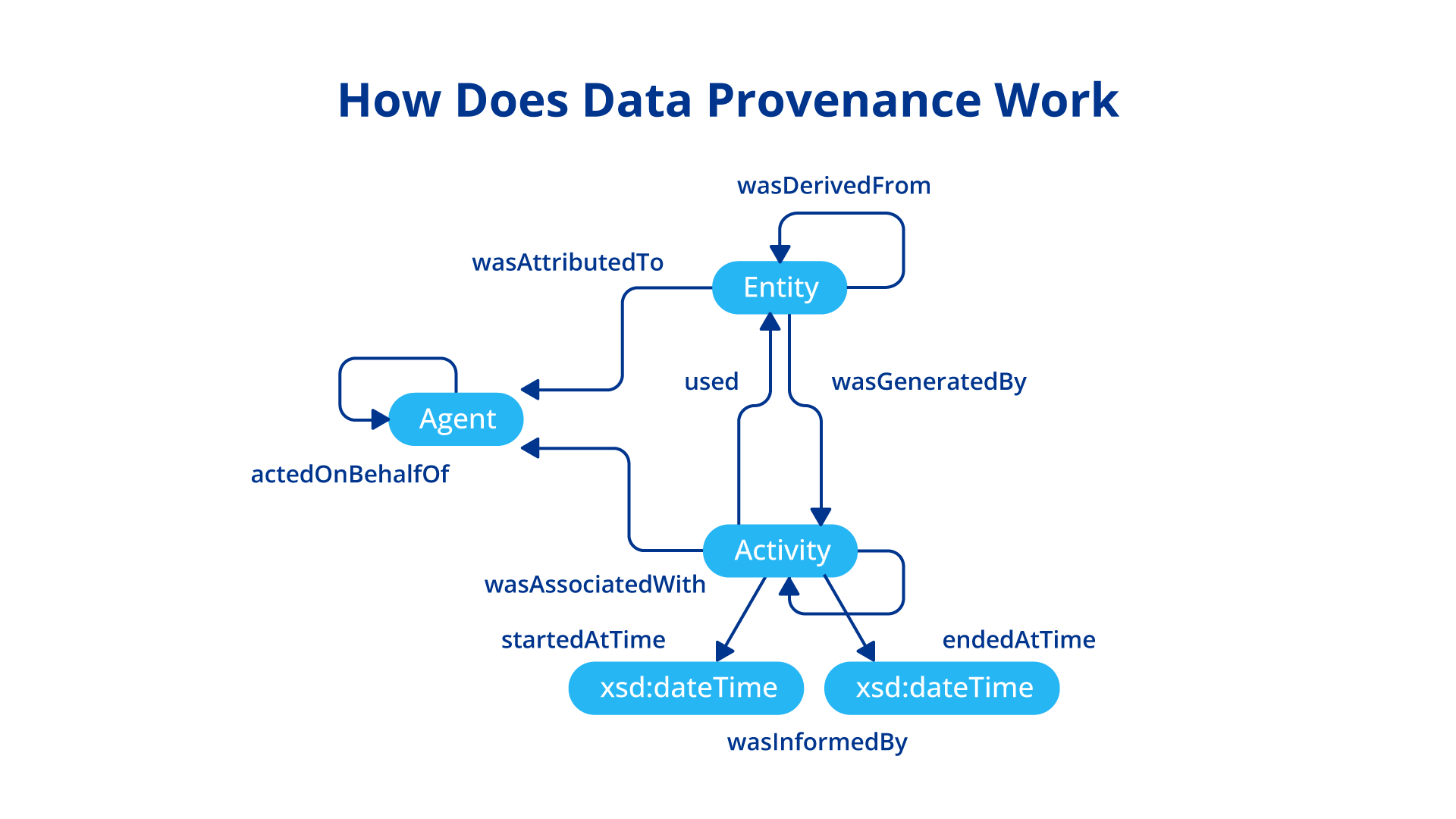
How Does Data Provenance Work?
Data provenance works as a system that utilizes various technologies to enhance the integrity and trustworthiness of the data. Following mechanisms define its effectiveness:
1. Metadata Management Systems
Metadata plays a crucial role in tracking the history of data. Modern metadata management systems, such as data catalogs and data governance platforms, store detailed records of data origins, transformations, and usage. These systems enable organizations to maintain an auditable trail, ensuring compliance with regulatory requirements like GDPR and HIPAA.
2. Blockchain for Immutable Data Provenance
Blockchain technology provides a decentralized and tamper-proof ledger that enhances data integrity. By recording each data transaction as a cryptographic block, blockchain ensures that any modification is traceable and verifiable. Industries such as supply chain management and finance leverage blockchain-based provenance to confirm data authenticity and prevent fraud.
3. Cryptographic Hashing for Data Integrity
Cryptographic techniques are mathematical tools to crawl and unscramble data for tamper-proof verification. Data provenance systems use cryptographic techniques for securing metadata and ensuring its immutability, which means that any change to data cannot go unnoticed.
Cryptographic hashing techniques, such as SHA-256, generate unique digital fingerprints for data at each stage of its lifecycle. Any unauthorized modification alters the hash value, immediately flagging potential data corruption. Cryptographic hashing is widely used in digital forensics, cybersecurity, and scientific research.
4. Distributed Ledger Technologies (DLT)
Beyond blockchain, other distributed ledger technologies (e.g., Hedera Hashgraph and IOTA) offer alternative mechanisms for secure data provenance. DLT provides real-time data tracking and validation without requiring a central authority, making it suitable for industries that require decentralized verification, such as healthcare and IoT.
DLT also supports controlled access, allowing authorized stakeholders to view the audit trail and confirm a data point’s history, promoting trust and collaboration in data ecosystems.
5. AI and Machine Learning for Automated Provenance Tracking
AI-powered systems can analyze large datasets and automatically generate provenance records by detecting patterns in data movement and transformation. Machine learning models help predict anomalies and flag inconsistencies in data lineage, enhancing governance in big data environments.
Organizations can leverage data provenance tools to enable easy verification and lineage tracking, using metadata and cryptographic hashes to check data authenticity and integrity.
Also, these tools provide user-friendly interfaces, allowing end-users to access and verify information directly. The ease of using such tools empowers people to assess the trustworthiness of their data confidently.
6. Cloud-Based Provenance Solutions
With the rise of cloud computing, platforms like AWS Data Lake, Azure Purview, and Google Cloud Data Catalog offer built-in provenance tracking capabilities. These tools enable organizations to maintain a centralized record of data origin, movement, and transformation, ensuring compliance with data governance frameworks.
By integrating these technologies, organizations can establish a reliable and verifiable data provenance framework that enhances transparency, security, and compliance across various industries.
Challenges in Implementing Data Provenance
While data provenance offers numerous benefits, organizations often face challenges when implementing it at scale. These challenges stem from technical, organizational, and regulatory complexities that require strategic solutions.
1. Managing Large-Scale Data Volumes
Modern enterprises generate vast amounts of data daily, making it difficult to capture, store, and manage detailed provenance records. The storage and processing demands of maintaining a complete data history can lead to performance bottlenecks and increased infrastructure costs.
Solution: Implement scalable metadata management systems and cloud-based storage solutions that efficiently handle large datasets while optimizing performance.
2. Ensuring Data Privacy and Compliance
Data provenance systems often require storing detailed records of data origins, modifications, and users involved in the process. This can pose privacy risks, particularly when handling sensitive information subject to regulations like GDPR, HIPAA, and CCPA.
Solution: Employ privacy-preserving techniques such as anonymization, access controls, and encryption to ensure compliance without compromising data security.
3. Standardizing Provenance Data Across Systems
Many organizations use multiple data platforms and tools, each with different ways of tracking provenance. This lack of standardization makes it challenging to create a unified, interoperable provenance framework.
Solution: Adopt industry standards such as W3C PROV (Provenance Data Model) or ISO 8000 to ensure consistency and compatibility across data systems.
4. Balancing Performance with Provenance Tracking
Tracking every data transformation and access event can slow down workflows, especially in high-speed data processing environments. Organizations must balance granularity with system performance to avoid disruptions.
Solution: Use selective logging and tiered provenance storage, where critical data transformations are tracked in detail while less significant events are recorded at a summary level.
5. Preventing Unauthorized Tampering of Provenance Records
Provenance data is only useful if it remains accurate and unaltered. Malicious actors or system errors can introduce inconsistencies, leading to mistrust in the provenance trail.
Solution: Leverage blockchain, cryptographic hashing, and immutable storage solutions to create tamper-proof provenance records that ensure data integrity.
6. Integrating Provenance Tracking into Legacy Systems
Many organizations still rely on legacy systems that lack built-in provenance tracking capabilities. Retrofitting these systems to support provenance can be complex and costly.
Solution: Use middleware solutions or API-based connectors to integrate provenance tracking into existing infrastructure without disrupting critical operations.
By addressing these challenges with the right strategies and technologies, organizations can successfully implement a robust data provenance framework that enhances data integrity, compliance, and reliability.
Best Practices for Implementing Data Provenance
While the challenges of implementing data provenance can seem daunting, they can be effectively managed with the right strategies. By adopting industry best practices, organizations can create a structured approach to data provenance, ensuring transparency, compliance, and data integrity.
The following best practices will help you address these challenges and build a robust data provenance framework:
1. Define Clear Provenance Goals
Before implementing a provenance system, identify the primary objectives. Are you tracking data lineage for regulatory compliance, ensuring data integrity, or improving analytics accuracy? Defining goals helps in selecting the right tools and methodologies.
Actionable Tip: Establish use cases such as regulatory reporting, anomaly detection, or AI model validation to guide your provenance strategy.
2. Automate Provenance Capture
Manually tracking data provenance is impractical, especially in large-scale environments. Automated tools can capture metadata, transformations, and access logs in real time without disrupting workflows.
Actionable Tip: Use data governance platforms, metadata management tools, or built-in logging features in ETL/ELT pipelines to automate provenance tracking.
3. Standardize Metadata Collection
Inconsistent metadata formats make it difficult to establish a unified provenance framework. Standardization ensures interoperability across different systems and platforms.
Actionable Tip: Adopt industry standards such as W3C PROV, ISO 8000, or DCAT (Data Catalog Vocabulary) to maintain uniform provenance records.
4. Implement Access Controls and Encryption
Provenance data often contains sensitive information, such as user actions and data origins. Unauthorized access can compromise security and lead to compliance violations.
Actionable Tip: Use role-based access control (RBAC), encryption, and audit logs to protect provenance records from unauthorized modifications.
5. Balance Granularity and Performance
Tracking every minor data change can create storage overhead and slow down performance. Determine the optimal level of detail needed for your use case.
Actionable Tip: Implement tiered tracking—store detailed provenance for critical datasets while using aggregated metadata for less significant transformations.
6. Ensure Immutability with Blockchain or Hashing
To maintain trust in provenance data, records must be immutable and tamper-proof. Blockchain and cryptographic hashing provide robust solutions.
Actionable Tip: Use blockchain for decentralized, verifiable provenance records or cryptographic hashing to detect unauthorized modifications.
7. Integrate Provenance with Data Governance
Provenance tracking should be an integral part of an organization’s data governance framework to ensure compliance and accountability.
Actionable Tip: Embed provenance policies into data governance workflows and align them with regulatory requirements like GDPR, HIPAA, and CCPA.
8. Enable Real-Time Monitoring and Auditing
Regular monitoring and auditing help detect anomalies in data provenance trails, ensuring ongoing data reliability and compliance.
Actionable Tip: Deploy dashboards and automated alerts to track changes, flag inconsistencies, and generate compliance reports.
By following these best practices, organizations can maximize the benefits of data provenance while maintaining security, compliance, and operational efficiency.
Enhance Your Data Transparency with Astera Data Pipeline Builder
Experience Astera's all-in-one, AI-powered data integration platform to maintain your data's integrity and trustworthiness. Start your 14-day free trial today and gain insight into your data's origin, movement, and transformations.
Start a FREE TrialData Provenance Use Cases
Data provenance has applications across various industries, helping organizations maintain data integrity, comply with regulations, and optimize operations. Here are some key use cases:
1. Regulatory Compliance and Audits
Industries such as healthcare, finance, and government must comply with strict regulations like GDPR, HIPAA, and SOX. Data provenance ensures organizations can provide a clear audit trail of data access, modifications, and usage, reducing compliance risks.
Example: A healthcare provider tracks patient data changes to comply with HIPAA regulations and prevent unauthorized access.
2. Fraud Detection in Finance and Insurance
Financial institutions and insurers use data provenance to detect anomalies in transactions and claims processing. By tracking data lineage, they can identify suspicious patterns and prevent fraudulent activities.
Example: An insurance company traces policyholder data to verify the legitimacy of a claim, preventing false submissions.
3. Supply Chain Transparency
Manufacturers and retailers use data provenance to monitor the flow of goods and raw materials across supply chains, ensuring ethical sourcing and quality control.
Example: A food manufacturer tracks ingredient sources to confirm compliance with organic certification standards.
4. AI and Machine Learning Model Integrity
AI-driven systems rely on high-quality data for accurate decision-making. Data provenance helps data scientists track data sources, transformations, and biases, ensuring AI models remain reliable.
Example: A financial institution audits AI-driven credit scoring models to verify that data inputs are unbiased and comply with regulations.
5. Scientific Research and Data Integrity
In research and academia, reproducibility is critical. Data provenance ensures that scientific datasets remain accurate, allowing researchers to validate and reproduce findings.
Example: A genomics lab tracks the lineage of DNA sequencing data to confirm the validity of its research results.
6. Cybersecurity and Incident Response
Provenance data helps cybersecurity teams detect unauthorized access, track data breaches, and investigate security incidents.
Example: A financial services firm identifies a data breach by tracking unusual changes to customer records.
Future Trends in Data Provenance
As data ecosystems continue to evolve, advancements in technology are shaping the future of data provenance. Here are some key trends to watch:
1. AI-Driven Provenance Tracking
Artificial intelligence (AI) and machine learning (ML) are increasingly being used to automate data lineage tracking, anomaly detection, and metadata management. AI-driven tools can provide deeper insights into data movements and flag inconsistencies in real-time.
2. Blockchain for Tamper-Proof Provenance
Blockchain technology is gaining traction as a secure method for tracking data provenance. By leveraging decentralized ledgers, organizations can create immutable audit trails that enhance transparency and prevent data manipulation.
3. Real-Time Provenance in Streaming Data Pipelines
With the rise of real-time data processing, provenance tracking is expanding beyond batch systems. Organizations are adopting streaming data lineage solutions to monitor changes instantly and ensure data integrity in dynamic environments.
4. Integration with Data Privacy Regulations
Regulatory bodies continue to impose stricter data governance requirements. Future data provenance systems will need built-in compliance features that align with GDPR, CCPA, HIPAA, and other frameworks, ensuring organizations can easily demonstrate data traceability.
5. Cloud-Native Provenance Solutions
As businesses shift to cloud-based infrastructures, provenance solutions are adapting to support hybrid and multi-cloud environments. Cloud-native tools provide centralized visibility into data movements across distributed systems.
6. Standardization and Interoperability
Industry-wide standards for data provenance are emerging to ensure interoperability between different platforms and tools. The development of standardized metadata frameworks will simplify data lineage tracking across diverse ecosystems.
Concluding Thoughts
As our dependency on data grows, utilizing data provenance methods and techniques to ensure trust in data is imperative. Data provenance equips organizations with tools to make informed decisions based on reliable information.
Astera Data Pipeline Builder is an AI-powered data integration platform that equips organizations with tools to track and analyze data movement. Data lineage feature allows the tracing and transformation of data assets, from source to destination. Also, impact analysis helps to identify how data is modified and utilized through various pipelines, enhancing the understanding of dependencies and potential risks associated with data changes.
Download a 14-day free trial to experience how Astera Data Pipeline Builder helps with data lineage and provenance.
 Astera AI Agent Builder - First Look Coming Soon!
Astera AI Agent Builder - First Look Coming Soon!

